Security Recently, detailed information has surfaced regarding a large-scale ad fraud operation leveraging hundreds of applications within the Google Play Store. This operation, codenamed “Konfety” (Russian for “candy”), exploits a mobile advertising software development kit (SDK) associated with the Russian ad network CaramelAds.
HUMAN’s Satori threat intelligence team, in a technical report shared with The Hacker News, stated: “Konfety represents a new form of fraud and obfuscation where threat actors operate ‘bait twins’ of applications alongside ‘evil twins’ on major markets.”
What are “Bait/Evil Twins”?
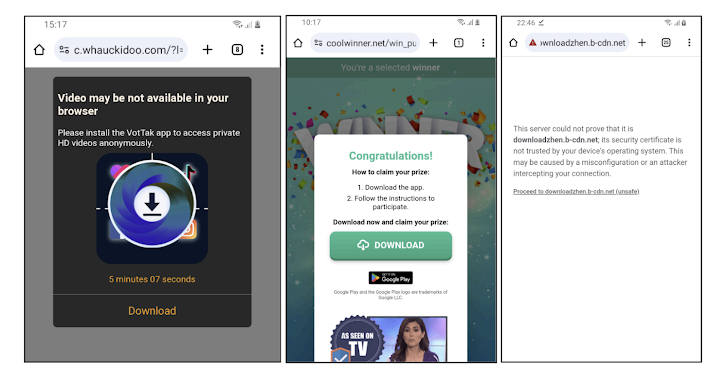
The most distinctive aspect of the Konfety operation is its use of a “bait/evil twin” mechanism. The bait applications (numbering over 250) are harmless and distributed through the Google Play Store. However, their “evil twin” counterparts spread through malicious ad campaigns, aimed at promoting ad fraud, monitoring web searches, installing browser extensions, and sideloading APK file code onto user devices.
Surprisingly, the evil twin applications mimic their bait twins by spoofing their application IDs and ad publisher IDs. Both bait and evil twin applications operate on the same infrastructure, allowing threat actors to scale their operations exponentially as needed.
Disguise of Bait Applications
While bait applications function normally and most do not display ads, they include GDPR consent notices. Their primary purpose is to act as cover for the evil twins. Researchers at HUMAN noted: “This bait/evil twin confusion mechanism is a new method for threat actors to disguise fraudulent traffic as legitimate. During peak periods, programmatic requests associated with Konfety reached up to 10 billion per day.”
Propagation and Operation of Evil Twins
Konfety’s evil twin applications spread through malicious ad campaigns that promote APK modules and other software like Letasoft Sound Booster. These campaigns leverage attacker-controlled domains, infected WordPress sites, and other content-upload platforms such as Docker Hub, Facebook, Google Sites, and OpenSea.
Users clicking these URLs are redirected to domains that deceive them into downloading malicious applications. These malicious apps serve as implanters in the first stage, decrypting from APK file assets and used for command and control (C2) communications setup.
In the initial stage, programs attempt to hide application icons on device home screens and execute fraud by running second-stage DEX payloads that display context-free full-screen video ads.
Network Traffic and Ad Fraud
Researchers highlighted: “The key to Konfety’s operation lies in its evil twin applications. These applications mimic their respective bait twins by replicating their application ID/package name and publisher ID.”
“Network traffic from evil twin applications functionally mirrors that from bait twins; impressions from evil twins use the package name of their bait twin counterparts.”
Other Malicious Features
Additional functionalities of this malware include exploiting the CaramelAds SDK to access websites via default web browsers, modifying versions of other ad SDKs through notification scams to deceive users into clicking on fake links or sideloading.
Moreover, users installing evil twin applications are prompted to add a search toolbar widget to their device home screens, which secretly monitors their searches by sending data to domains named vptrackme[.]com and youaresearching[.]com.
Conclusion
Researchers concluded: “Threat actors know that hosting malicious applications in stores isn’t a sustainable technique, and they are looking for creative and cunning ways to evade detection and perpetrate sustained, long-term fraud. Establishing intermediary SDK companies and distributing SDKs to abuse high-quality publishers is an increasingly popular technique.”
The Konfety incident serves as a reminder that mobile app security continues to face significant challenges. Users and developers need to remain vigilant against potential threats to ensure the security of devices and data.